Data Security & Data Privacy Management System
In the era of informatization, data has become one of the most valuable assets for enterprises. However, with the rapid growth of data and the continuous development of technology, enterprise data security is facing unprecedented challenges. Therefore, mastering key data security technologies and applying them in combination with practical cases is crucial for ensuring enterprise data security.
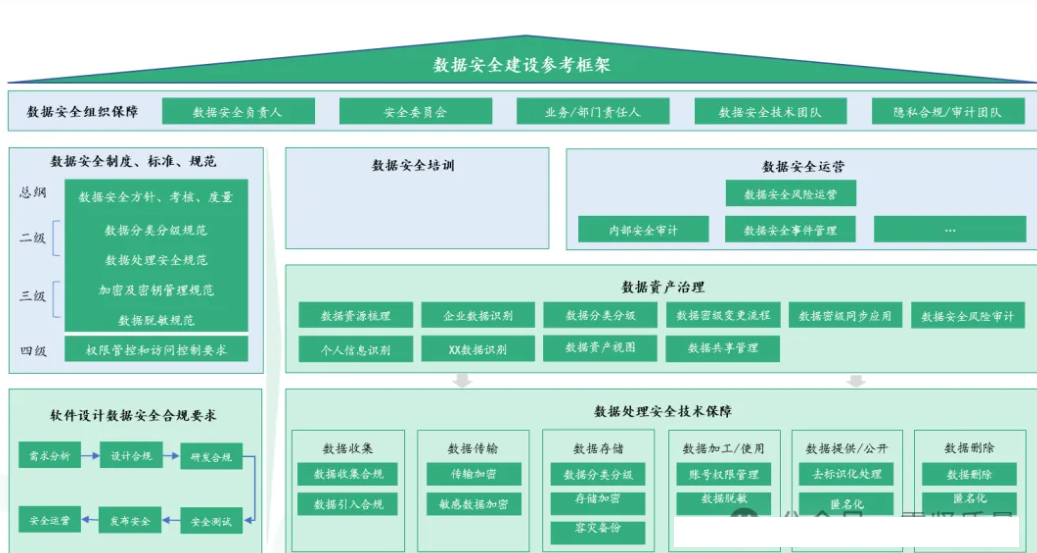
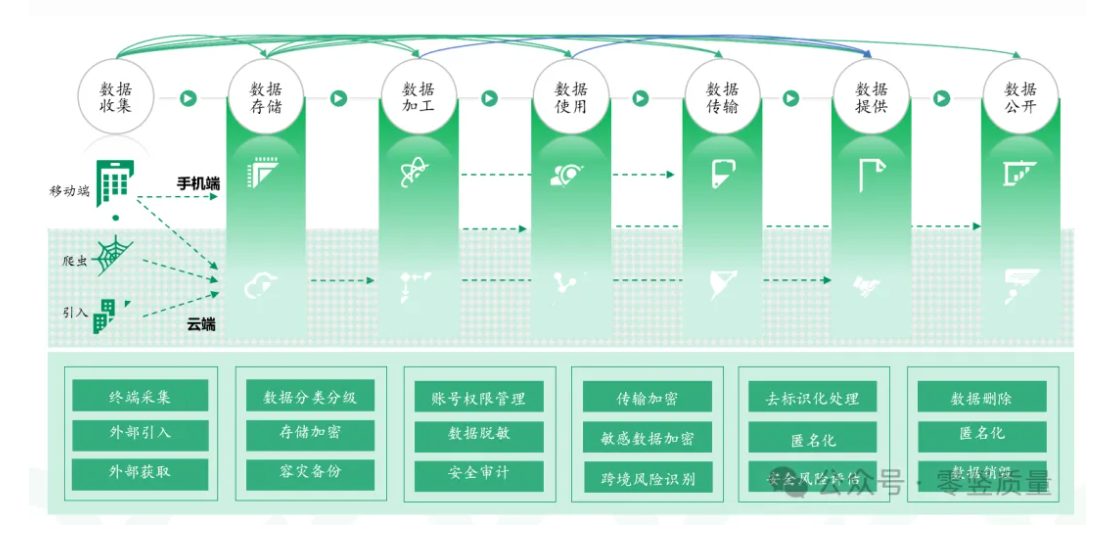
Key Technologies for Enterprise Data Security
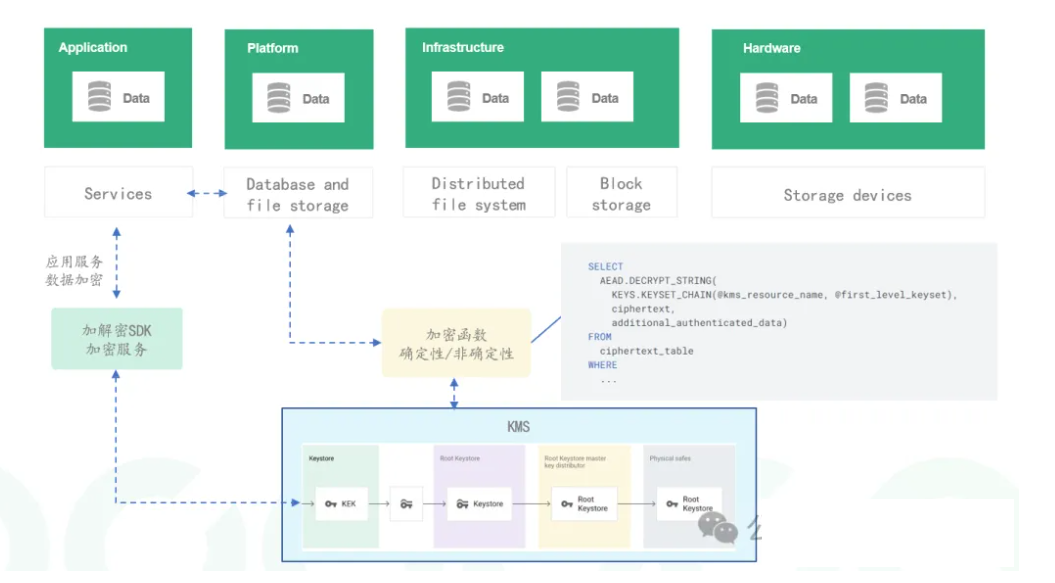
1. Data encryption technology
Data encryption is one of the important means to ensure data security. By using symmetric encryption, asymmetric encryption and other algorithms to encrypt sensitive data, the confidentiality of data during transmission and storage can be ensured. Meanwhile, by combining access control and permission management, strict restrictions on data access can be implemented to prevent data leakage and illegal access.
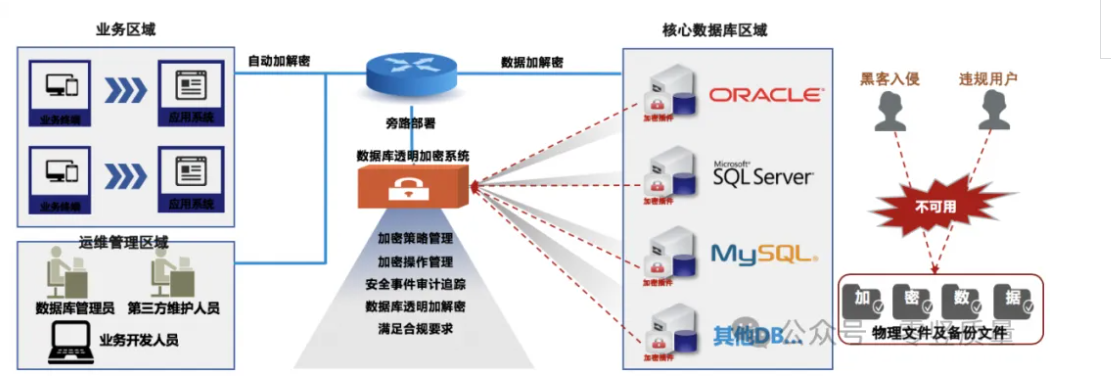
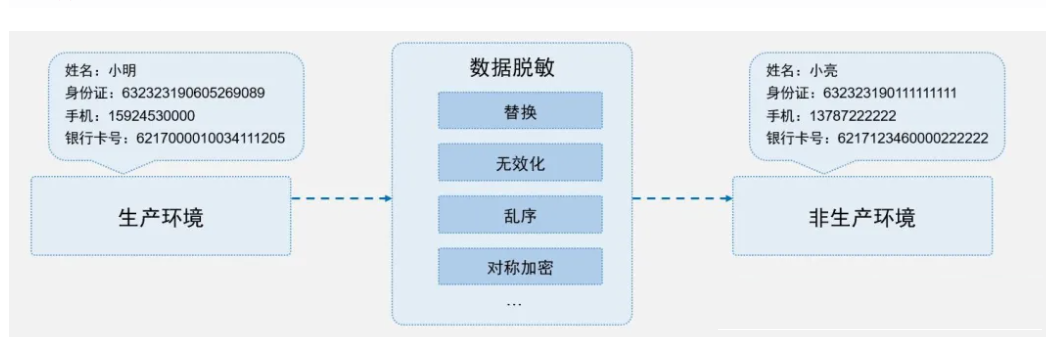
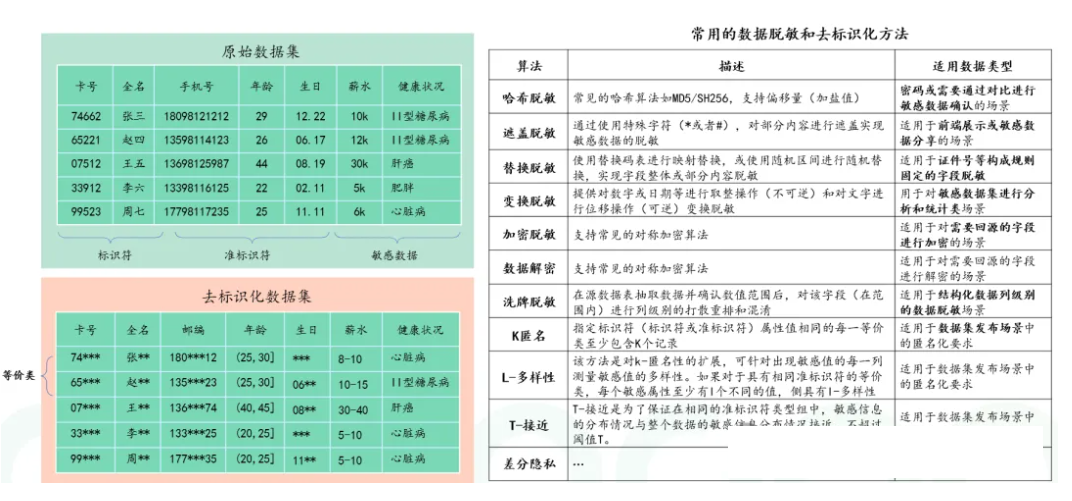
2. Data Desensitization & Data masking Technology
Data desensitization is a technology that aims to protect data privacy and security by modifying or deleting key information in sensitive data. By desensitizing data, enterprises can reduce the risk of sensitive data leakage without affecting normal business operations. Meanwhile, data desensitization can also be used in testing and development environments to avoid the misuse of sensitive data during the development process.
3. Data backup and recovery technology
Data backup and recovery is one of the important measures to ensure data security. By regularly backing up data and promptly restoring it in the event of data loss or damage, the losses caused by data loss can be minimized to the greatest extent possible. Meanwhile, combined with disaster recovery plans, enterprises can quickly restore business operations in the event of a serious failure or disaster.
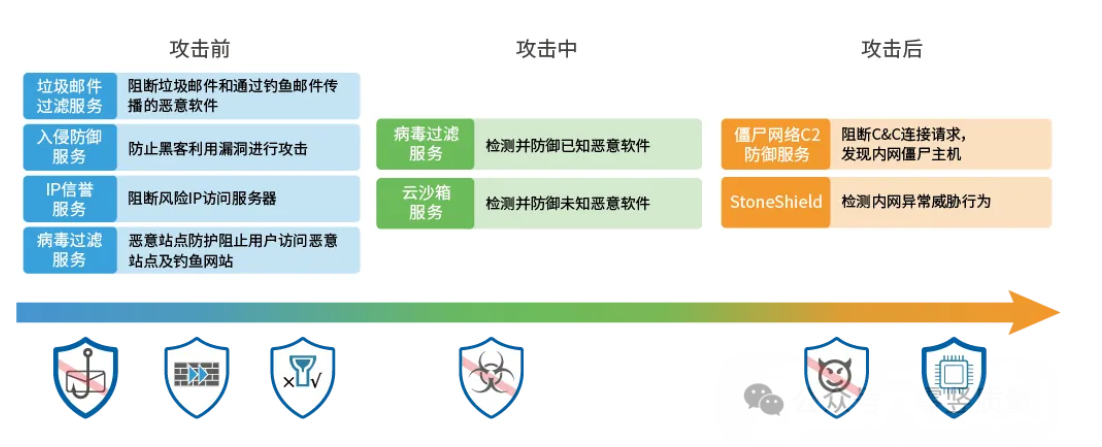
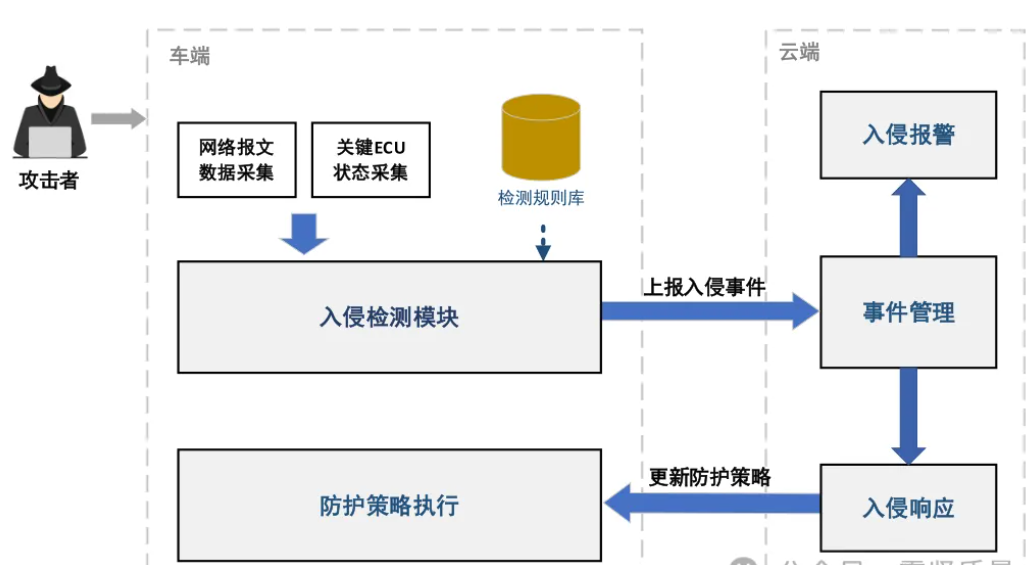
4. Intrusion detection and defense technology
Intrusion Detection and Defense Systems (IDS/IPS) can monitor network traffic and system behavior in real-time, detect and prevent potential security threats in a timely manner. By using techniques such as pattern matching and behavior analysis, IDS/IPS can identify abnormal traffic and attack behavior, and take corresponding defense measures to protect enterprise data from attacks.
Customer Case
Taking a large e-commerce enterprise as an example, it faces a massive amount of user and transaction data, with extremely high data security risks. In order to ensure data security, the enterprise has adopted the following key technologies and practical measures:
1. Comprehensive data encryption
The enterprise has comprehensively encrypted all sensitive data, including user personal information, transaction records, etc. By adopting advanced encryption algorithms and key management mechanisms, the confidentiality of data during transmission and storage is ensured. At the same time, by combining access control and permission management, strict restrictions on data access have been implemented to prevent data leakage and illegal access.
2. Flexible data desensitization
In order to meet the data privacy protection needs in different scenarios, the enterprise has adopted flexible data desensitization technology. In testing and development environments, the risk of misuse and leakage of sensitive data is avoided by desensitizing it. At the same time, in data sharing and cooperation, data desensitization technology has been used to achieve secure sharing and utilization of data.
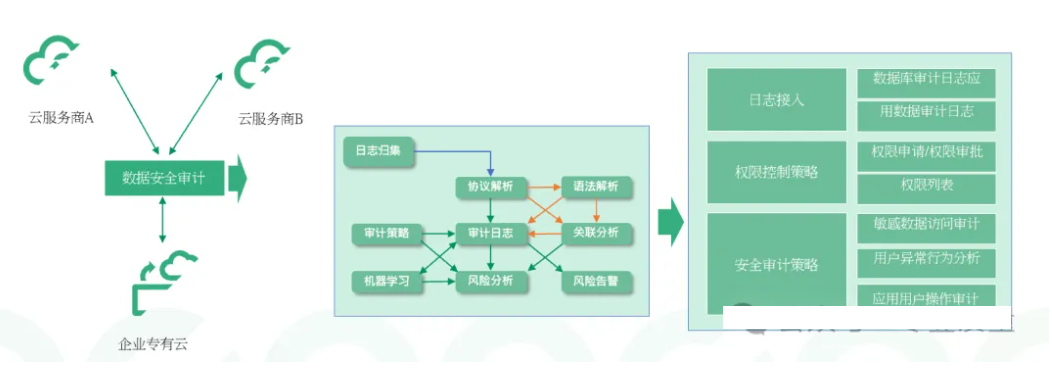
3. Comprehensive data backup and recovery system
The enterprise has established a comprehensive data backup and recovery system, including regular backups, remote backups, and rapid recovery mechanisms. By regularly backing up data and promptly restoring it in the event of data loss or damage, business continuity and data integrity are ensured. At the same time, combined with a disaster recovery plan, the enterprise can quickly restore business operations in the event of a serious failure or disaster.
4. Intelligent intrusion detection and defense
The enterprise has deployed an intelligent intrusion detection and defense system that can monitor network traffic and system behavior in real-time. By adopting machine learning and artificial intelligence technologies, IDS/IPS can automatically identify abnormal traffic and attack behavior, and take corresponding defense measures. In addition, the company has established a comprehensive safety emergency response mechanism, which can quickly respond and handle safety incidents.
By mastering key data security technologies and applying them in combination with practical cases, enterprises can effectively ensure data security, reduce the risk of data leakage and illegal access. In the future development, with the continuous progress of technology and the expansion of application scenarios, enterprise data security will face more challenges and opportunities. Therefore, enterprises need to continuously strengthen the research and practical application of data security technology to cope with increasingly complex security threats and challenges.
StarNET© Technology Co., Ltd
913, Building B, Ruichuang International Center, No. 8 Wangjing East Road, Beijing +86 10 68876296
info@starnet-data.com
Website:www.starnet-data.com
WeChat No: starnet-2013
