Hunan Big Data Command and Operations Platform
Building a "big data holographic information warfare command platform" with Hunan characteristics; Integrate and utilize the big data resources and other social basic data resources integrated within the Hunan government, according to the actual needs of Hunan's overall business, to achieve some practical functions such as intelligent archives, target management, trajectory tracking, discovery and warning, data reconnaissance, command and dispatch, and lay a solid foundation for achieving holographic information warfare command across all sectors of Hunan.
1. Solution Objectives
1) Utilize the data resources of the technical investigation data center to construct a smart archive system that includes people and objects
2) Build a classified and graded target management system that meets the needs of reconnaissance, case handling, and enemy reconnaissance
3) Innovate working methods, utilize data-driven business, and build an automated linkage warning and command system
4) Establish a user, data, and application management system that is integrated with the existing authentication system; Building GIS Geographic Location Information Basic Services
5) Integrate and integrate multiple business functions from the data and application levels, and initially form a holographic information warfare command system based on big data architecture
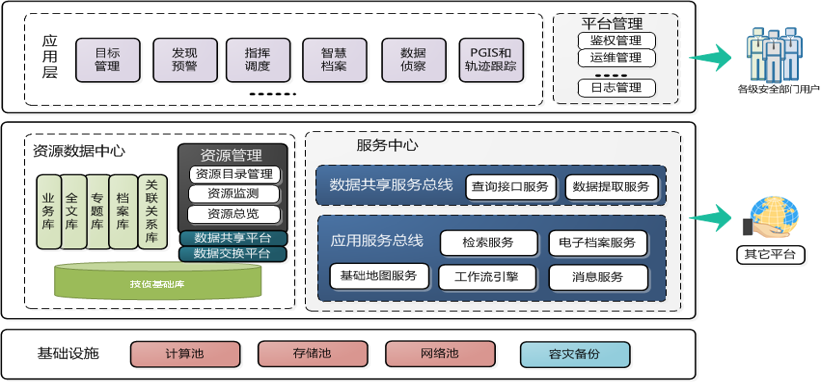
2. Overall Technical Architecture
3. System Core Technology
1). Unique hybrid architecture efficient big data storage analysis engine and Big Data SQL intelligent aggregation query technology:Supported by a hybrid architecture of distributed data big data engine (Hadoop/Park) and high-performance relational databases.
Support TB level structured and unstructured data storage and analysis. Big Data SQL provides second level transparent data query and access capabilities across Hadoop clusters and relational databases using standard SQL for trillions of data volumes.
2). Flexible business modeling analysis based on graphical modeling and workflow analysis engine: Based on the WYSIWYG graphical approach, users are provided with the ability to establish various business analysis models. Analysis users can complete the establishment of complex business models by dragging and dropping various data sources and model nodes (queries, comparisons, associations, statistics, set operations, data mining, model scoring, report export, etc.). Based on workflow analysis engine technology, complex multi-step business analysis model modeling and task scheduling execution are supported.
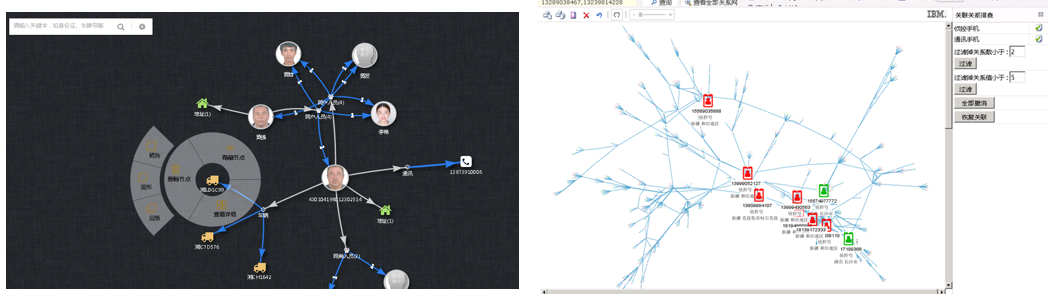
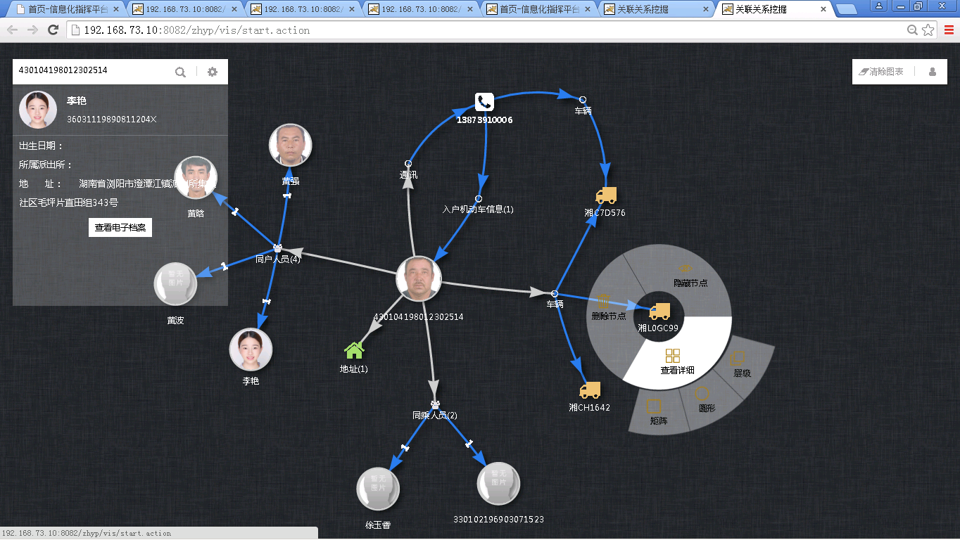
3). Visual correlation analysis and relationship graph technology based on graph databases: Visualize various massive business volumes in big data systems in a graphical manner (network layout, grouping layout, hierarchical layout, time series layout, topic row layout), and use various visual analysis methods to discover various relevant information involved in the analysis elements, as well as cross correlations and relationship graphs between various data.
4). Heterogeneous data integration from open data sources and multi-dimensional data modeling technology for intelligence clues: Realize the cleaning, classification, integration, correlation, and database building of various clues and resource data obtained by the public security department; Build a multi-dimensional holographic clue thematic library with human, object, and other elements as the core. This includes entity and relationship extraction, automatic clue classification, clue mapping, clue indexing, clue association settings, and automatic clue maintenance.
5). Holographic intelligent archive technology based on intelligent data association and user profiling: By using intelligent data association and entity association extraction, various business analysis elements such as key personnel, items, code addresses, and case materials can be automatically collected and classified. Corresponding electronic archives can be established to combine historical archives with dynamic archives, providing support for dynamic control of key personnel, major event warning and prevention, comprehensive analysis, and other applications.
6). Data reconnaissance business model technology based on data mining and machine learning algorithms:Deeply utilizing existing big data resources, using data mining and machine learning algorithms to support various complex data reconnaissance model processing, including adjoint analysis, deep comparison analysis, relationship network analysis, spatiotemporal trajectory analysis, internet browsing habit analysis, network social behavior analysis, relationship graph analysis, abnormal behavior analysis, connectivity habit analysis, hot event analysis, group object analysis, etc.
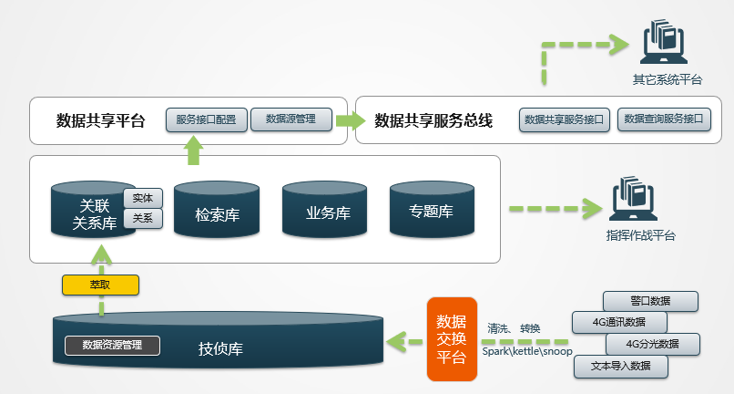
4. System Data Architecture Design
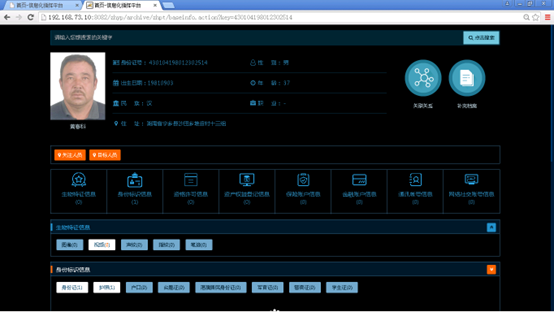
5.1 Smart Archives
Establish digital electronic archives centered around people and objects; By constructing a smart archive system, the basic and critical information of people and objects can be automatically collected and classified, corresponding electronic archives can be established, and dynamic updates of archives can be achieved, providing basic support for other functional modules of the holographic information warfare platform.
5.2 Target Management
Scientifically and intelligently manage target objects, etc. Define the data concepts and standards of each element according to the same logic for the goals that need to be focused on or carried out, and establish a classification and grading management system; Covering the entire reconnaissance and case handling workflow, achieving the informatization and standardization of target object management, and improving work efficiency and level.

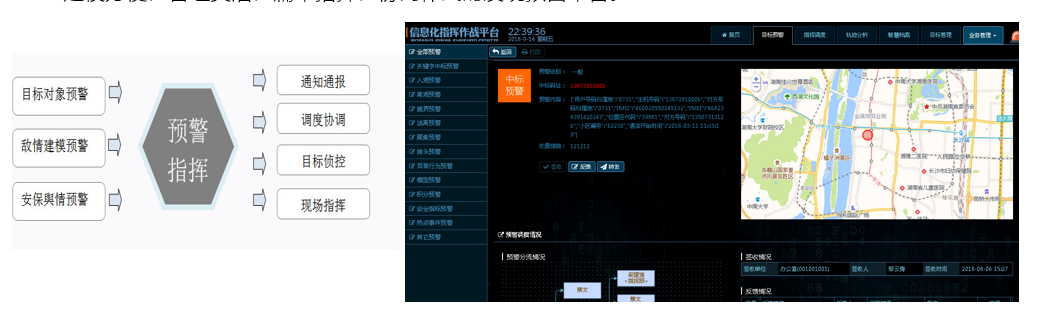
5.3 Discovery Warning
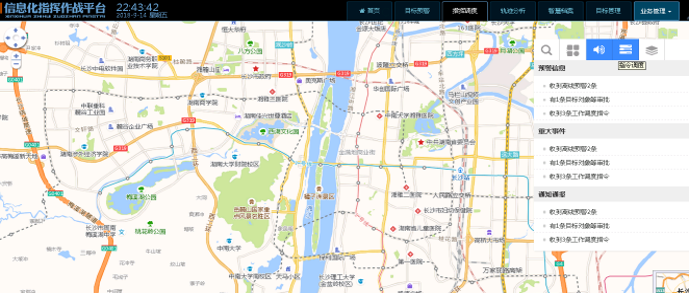
By comprehensively connecting various system data sources and basic data sources, under the guidance of enemy modeling and target object libraries, timely detection and distribution of enemy situations can be achieved, providing a system linkage, full database mining, easy docking, rapid response, timely and effective modeling, flexible management, flat command, and collaborative combat detection and early warning platform. The business functions mainly include content based and behavior based bid warning, data model-based warning, intelligent perception based warning, and warning process management
5.4 GIS and Trajectory Tracking
Provide basic GIS services to support all data analysis and result display that require geographic information support in the system. Realize target trajectory tracking, provide acquisition, visual display, and analysis of target activity trajectories. By analyzing data from multiple data types, comprehensively grasp the activity situation and action intention of the target.
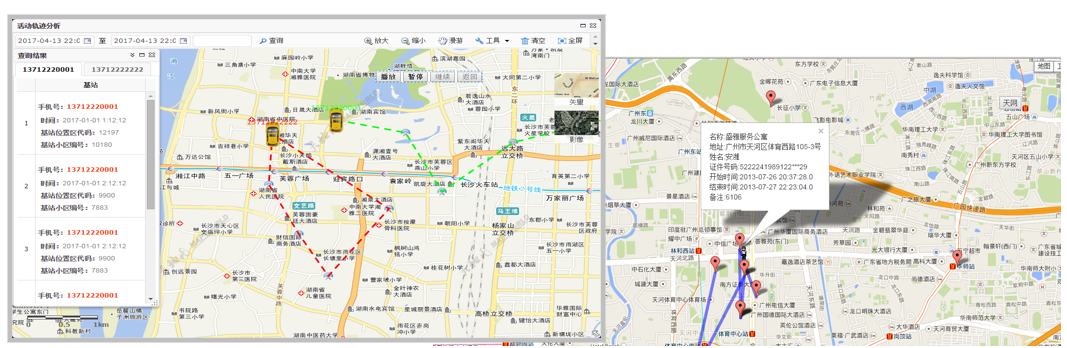
5.5 Data Reconnaissance
Deeply utilize the existing resources of the system, based on functional modules such as smart archives, target management, discovery and warning, to achieve data reconnaissance applications. Expand the utilization of personalized resources, achieve integration with system data for computational processing, and comprehensively enhance the ability and level of detection and strike. The business functions include companion analysis, deep comparison analysis, relationship network analysis, spatiotemporal trajectory analysis, and network social behavior analysis.
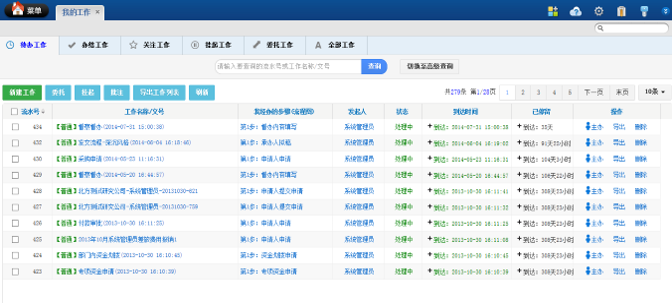
5.6 Workflow and Knowledge Base Management
Establish workflow management standards, improve the informatization level of workflows, and construct a business knowledge graph. According to the actual needs of business workflow, support flexible configuration of business workflow, support concurrent and cross node flow of multiple tasks, cover all work areas, and support subsequent upgrades and flexible expansion.
5.7 Command & Dispatch
Integrate various tasks and processes from reconnaissance activities to intelligence information into a unified interface, and initially form an integrated combat platform that supports the command and dispatch of the entire hall. The specific implementation goals include early warning event scheduling, intelligence information scheduling, reconnaissance and defense operation scheduling, visual command, etc.
 5.8 System Configuration Management and Operations Security
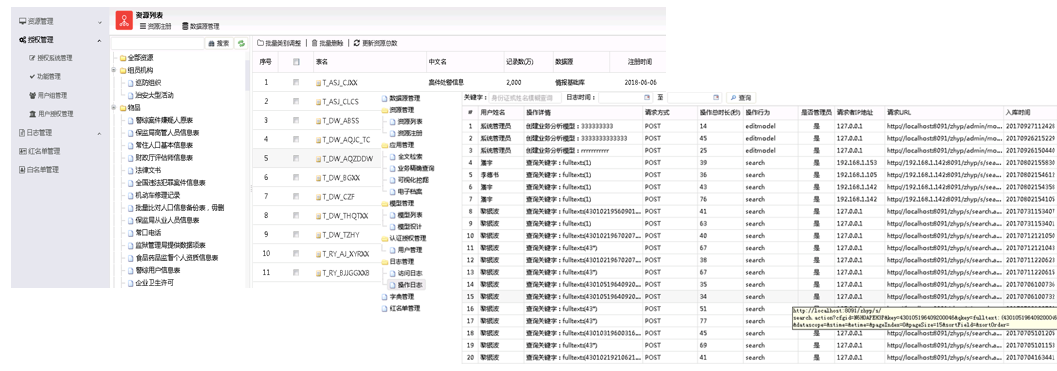
5.8 System Configuration Management and Operations SecurityImplement platform resource configuration, authentication management system, user permission management, log audit management, system security prevention management, etc.
StarNET© Technology Co., Ltd
913, Building B, Ruichuang International Center, No. 8 Wangjing East Road, Beijing +86 10 68876296
info@starnet-data.com
Website:www.starnet-data.com
WeChat No: starnet-2013
